Cyber Insurance Technologies
That Drive Growth
Cyberwrite’s patented cyber insurance models deliver next-generation catastrophe modeling and deep, data-driven insights for underwriting and cyber insurance brokers. Risk and Insurance professionals gain the clarity needed to assess exposure, control accumulation, reduce risk, and confidently support sustainable growth.

TRUSTED BY INDUSTRY LEADERS
Understanding cyber insurance risk is complicated. We make it easy.
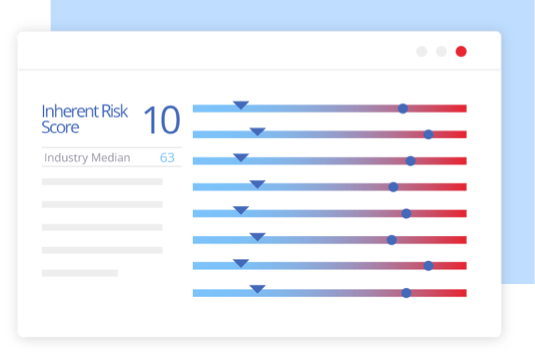
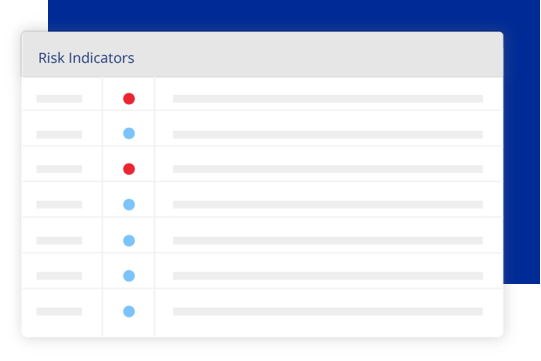

Designed for cyber insurance
Unparalleled Accuracy
Deep Insight
Broad Scope
Tailored to Coverage
Global Reach
REAL-WORLD IMPACT
320m+
Data in less than a minute on 320M+ businesses
80K+
Cyber Catastrophe Modeling Event Set
One platform to accelerate value across the cyber insurance lifecycle

For insurers
Increase Underwriting Profitability
Reduce underwriting costs and achieve record-low loss ratios with faster, more consistent underwriting decisions.
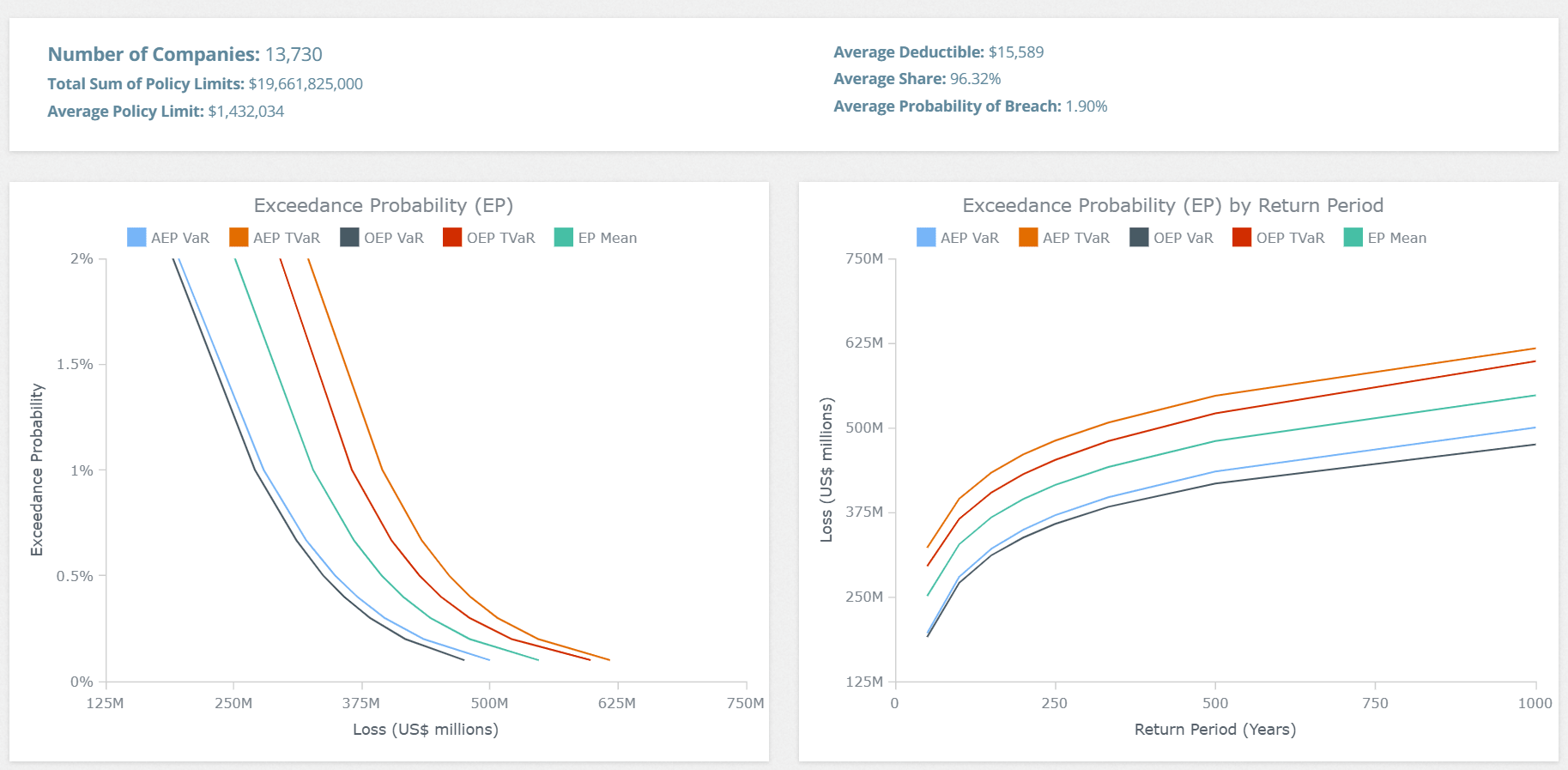
Improve Catastrophe Modeling
Gain greater visibility into your organization’s aggregated risk exposure and ongoing monitoring of each company’s risk.
Boost Distribution Efficiency
Better target sales efforts with cyber risk insights on any business, at any time.
Empower Insureds
Provide insureds with actionable insights to reduce their cyber risks and mitigate losses when cyberattacks do occur.

For reinsurers + Lloyd’s Syndicates
Data-Driven Catastrophe Modeling
Get the cyber insurance risk data you need for every company across your portfolio to improve catastrophe modeling and risk management.
Ensure Global Consistency
Provide easy-to-understand cyber risk reports to your cedent companies to ensure consistency in underwriting.
Empower Insureds
Provide insureds with actionable insights to reduce their cyber risks and mitigate losses when cyberattacks do occur.
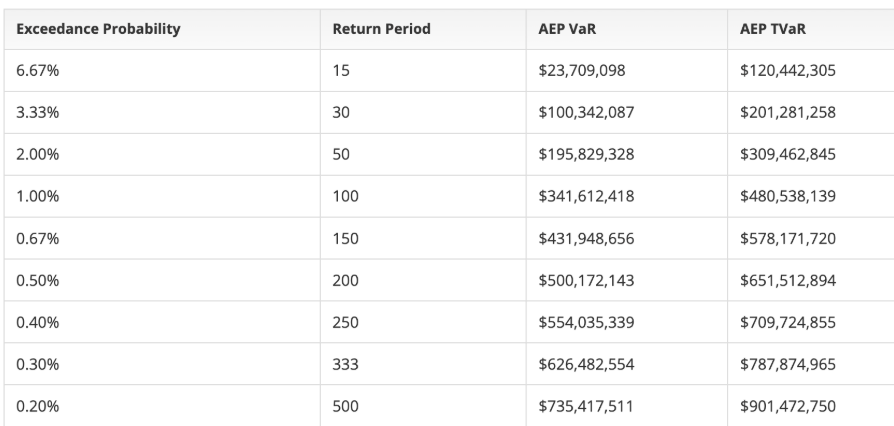
Catastrophe Modeling
Cyberwrite’s next-gen catastrophe model uses granular data on every risk to assess breach probabilities and potential damages accurately.

For brokers & MSSP’s
Grow Your Business
Become a trusted cyber risk advisor with personalized cyber insurance risk reports on any business in seconds to help your clients understand their cyber risks
Accelerate Sales
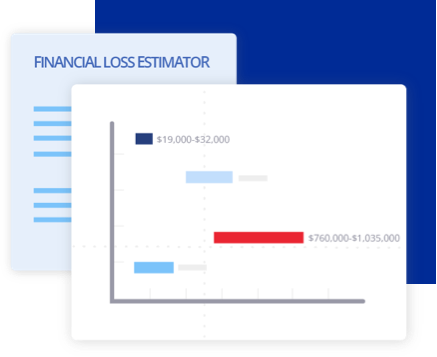
Drive adoption with ability to provide clients in real-time a clear understanding of the potential financial impact of a cyberattack on their business.
Empower Your Clients
Provide insureds with actionable insights to reduce their cyber risks and mitigate losses when cyberattacks do occur.
Reduce E&O Risks
Easily highlight the minimum coverage recommended to show clients why they need cyber insurance coverage.